NIST CSF For Everyone!
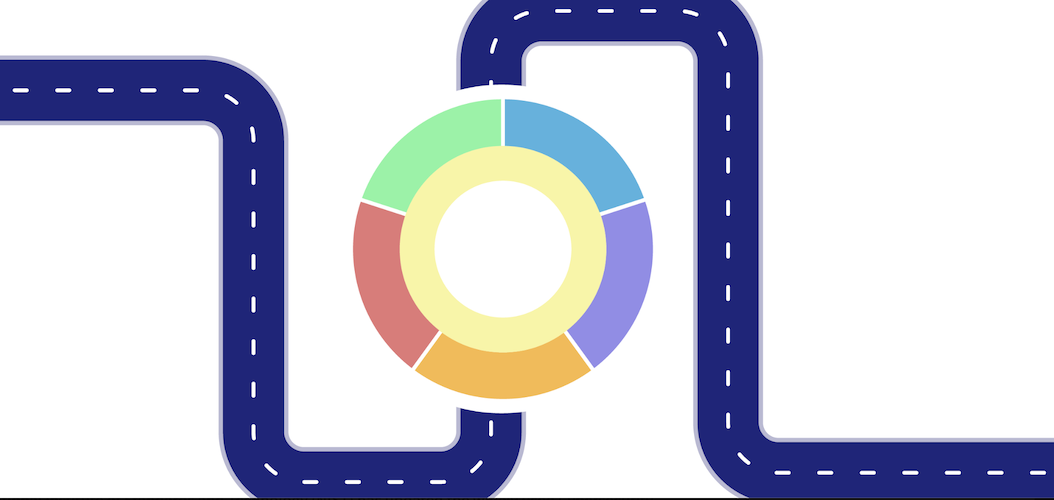
SOURCE: NIST
It's not just for professionals that work in critical infrastructure anymore. More roads now lead to NIST’s cybersecurity framework which can be used by all types of organizations to manage and reduce risks.
In February of 2024, NIST released version 2.0 of their Cybersecurity Framework, NIST CSF 2.0. This is the first major update since its creation back in 2014. All businesses and organizations now have a suite of resources that can help them achieve their cybersecurity goals, with added emphasis on governance.
So what does this mean for you and your business? Don’t sweat it, we’re here to help.
First, some background
If you're less familiar with NIST and CSF...
NIST is the National Institute of Standards and Technology, a government agency that is part of the U.S. Department of Commerce. More than a decade ago, NIST was tasked by Executive Order (EO 13636) with developing a framework to reduce risks to critical infrastructure. This resulted in the first Cybersecurity Framework called NIST CSF.
At its core, NIST CSF was created to reduce cybersecurity risks and help organizations better manage them. Although the first version of the framework was communicated as a tool for people in any sector or community – the real target audience was those working in the public sector.
“Developed by working closely with stakeholders and reflecting the most recent cybersecurity challenges and management practices, this update aims to make the framework even more relevant to a wider swath of users in the United States and abroad,”
Kevin Stine, chief of NIST’s Applied Cybersecurity Division.
That brings us to the update, NIST CSF 2.0, a cybersecurity framework that can be used by all types of organizations to:
- Increase clarity
- Address changes in technologies and risks
- Improve alignment with national and international cybersecurity standards and practices
What’s new? What’s different?
Version 2.0 brings numerous additions, removals, or modifications across the framework’s
- Functions
- Categories
- and Subcategories
Although the update is comprehensive, we think certain changes are particularly noteworthy and worth highlighting.
1. IMPLEMENTATION EXAMPLES
Out of everything that’s new, “Implementation Examples” might be one of the most helpful. NIST CSF 2.0 includes illustrative examples for each of its Subcategories, making the framework more actionable and user-friendly than before.
For example, if a Subcategory reads that an organization identifies vulnerabilities then an Implementation Example might read that the organization regularly conducts vulnerability scans to identify unpatched or misconfigured software.
A few more include:
| FUNCTION | CATEGORY | SUBCATEGORY | IMPLEMENTATION EXAMPLE |
| Govern |
Organizational Content (GV.OC) |
The organizational mission is understood and informs cybersecurity risk management | Ex1: Share the organization’s mission (e.g., through vision and mission statements, marketing, and service strategies) to provide a basis for identifying risks that may impede that mission |
| Protect |
Identity Management, Authentication, and Access Control (PR.AA) |
Identities are proofed and bound to credentials based on the context of interactions | Ex1: Verify a person’s claimed identity at enrollment time using government-issued identity credentials (e.g., passport, visa, driver’s license) Ex2: Issue a different credential for each person (i.e., no credential sharing) |
| Respond |
Incident Management (RS.MA) |
Incident reports are triaged and validated |
Ex1: Preliminarily review incident reports to confirm that they are cybersecurity-related and necessitate incident response activities |
| Recover |
Incident Recovery Plan Execution (RC.RP) |
The integrity of backups and other restoration assets is verified before using them for restoration | Ex1: Check restoration assets for indicators of compromise, file corruption, and other integrity issues before use |
This really helps take the guess work out of how to apply the framework. The list is quite comprehensive and can be downloaded as a PDF or Excel spreadsheet directly from NIST’s website.
2. GOVERNANCE
The other notable change in version 2.0 is the emphasis on governance. How much emphasis you might be wondering? Quite a bit. NIST added govern as a function, bringing the total number of functions to six. But before you think of this addition linearly, the govern function sits on top of the previous five functions.

SOURCE: NIST
Why was it added? The Govern function helps organizations prioritize actions across the other five areas, assign roles and responsibilities to encourage tighter procedures, and achieve oversight into cybersecurity strategy.
It’s kind of like taking the voice of each of the five functions and making sure there is a cohesive story to be told. If the other functions cover the actions a cybersecurity team needs to take, then the Govern function provides guidance for organizing a team that gets those things done in a consistent manner and without contradicting other efforts.
3. RESPOND AND RECOVER
Reflecting on the early days of NIST CSF and even version 1.1, the Respond and Recover functions didn’t get much spotlight. Now, with NIST CSF 2.0, there’s a stronger focus on these areas, emphasizing the need for cyber-resilient systems that not only prevent attacks but also ensure quick recovery.
This shift makes sense given today’s landscape. Cyber threats are more complex now compared to 2014. These days, it's not about if you’ll face a ransomware attack, but how you’ll respond when it happens. Back in the early 2010s, the main concern was resuming business operations after a natural disaster. Today, companies can shift their knowledge workers to remote setups and keep things running smoothly.
And while businesses adapt to evolving threats, cybercriminals are also getting more sophisticated. For example, many now use dual extortion tactics, where they not only encrypt your data but also threaten to release it if the ransom isn’t paid. This heightened level of threat is why there’s a greater emphasis on Respond and Recover in the latest version of the framework.
Now what?
If you’re already well-versed in the world of NIST CSF, Secure Compliance Solutions can be an extra pair of hands to help you achieve your cybersecurity goals and identify where you’re no longer compliant with version 2.0.
If you’re completely new to the framework, SCS can help you map out everything from start to finish so you can identify where you’re compliant, where you’re not and then what to do about it. We can demystify NIST CSF and make cybersecurity less intimidating overall.
“CSF 2.0 is not just about one document. It's about a suite of resources that can be customized and used individually or in combination over time as an organization’s cybersecurity needs change and its capabilities evolve.”
Laurie E. Locascio, Under Secretary of Commerce for Standards and Technology and NIST Director
A great resource for anyone new to NIST CSF or those of you with modest to no cybersecurity plans in place, check out NIST's quick start guide for small businesses.
-------------------------------------------
Need help navigating NIST CSF 2.0? We're here to answer your questions and get you on the right path. Call 708-593-3516 or email us info@scsprotect.com
Recent Posts
Posts by Month
- October 2025 (1)
- June 2025 (2)
- April 2025 (2)
- March 2025 (1)
- February 2025 (1)
- January 2025 (1)
- November 2024 (1)
- October 2024 (1)
- August 2024 (1)
- June 2024 (1)
- April 2024 (2)
- February 2024 (1)
- October 2023 (1)
- February 2023 (1)
- November 2021 (2)
- October 2021 (1)
- December 2020 (2)
- November 2020 (2)
- October 2020 (4)
- September 2020 (1)
- August 2020 (1)
- July 2020 (1)
- June 2020 (1)
- May 2020 (1)
- April 2018 (1)
- March 2018 (5)
- February 2018 (3)
- January 2018 (5)
- December 2017 (3)
- November 2017 (3)
- October 2017 (6)
- May 2017 (1)
- January 2016 (3)
- November 2015 (1)
- October 2015 (1)
